HUGE UPDATE: Read my updated article and wotc’s official statement. Great work, wotc, for your willingness to investigate this matter, and thanks to everybody who helped prove this scam.
I am an “on-again, off-again” MTGO fan. Since the release of version 3, I have been pretty much 100% “off-again” due to some of the bugs and the really awful UI I’ve found. But one thing I did decide to do was purchase a trade bot to deal with my old collection that could potentially get me a couple hundred dollars that could be put to better use than merely sitting around in my account.
I purchased CBSBot. But I’m paranoid, so I tend to carefully watch what’s going on with network traffic when running a third-party application that has access to an account that, to me, is worth a little bit of money and time. Using Wireshark, I analyzed the http traffic by setting a filter on port 80 (“tcp.port == 80” in the filter field):
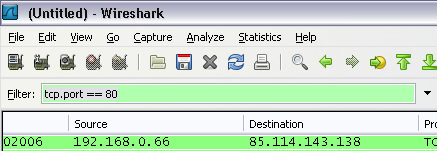
In version 1.29, I didn’t see any issues. Things were contacting the author’s server a bit too much for my tastes, but nothing dangerous seemed to be going on. I did, however, disable the connection to his server just to be safe. Who knows when something might pop up, right?
Well, when I got a hold of version 1.31, something did indeed pop up. Maybe it was in 1.30, but I can’t be sure since I never bothered downloading it. Anyway, immediately after launching the app, here’s what I saw in wireshark:
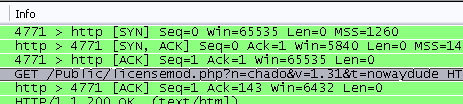
For those who don’t see exactly what’s going on, the bot is requesting a PHP script called “licensemod.php”, and sending my bot’s name, chado as argument n, and my (previous) password, nowaydude as argument t. This means that script can do ANYTHING with the password. It could be just using it for internal auditing for all I know, but it could also be storing it for later use.
Well, I wasn’t really sure what to do at this point. The bot is working for me, and I know how to keep it from contacting the site, but what about others running the bot? I first looked at it as “not my problem”, but then I saw on the author’s site that he’s preparing a defensive strike of some kind. I don’t know his plans, but right now he’s put up this warning CLAIMING that some people are getting an illegal version of his bot that has a back door and that it’s stolen 7 accounts already. He’s claiming that the “real” bot is 100% safe and doesn’t have a backdoor password! In my mind the only possibly plans he could have are to steal accounts and then say, “I did warn you guys about this.”
If you or somebody you know runs a bot for Magic Online, I urge you to TEST my theory. Download Wireshark and view the traffic. If that’s too complex, check out my instructions for spoofing my site as cardboostershop.com. By making the bot hit nerdbucket.com instead of cardboostershop.com, you can run the bot and then view that page again and see that the username and password you typed in were indeed sent directly to my server.
Obviously the first thing you should do is change your MTGO password.
UPDATE (2008-10-12): As I posted in comments below, 1.32 no longer sends the password, but instead a dummy string. The string is always the same no matter your username, password, or any other settings as far as I can tell.
At first I thought this was good news, but then I realized the other backdoors were probably still there. After some verification, I have discovered that there are indeed other backdoors:
- Several accounts can type in “pass” during a trade session, and the bot will send back your current password.
- Several accounts can type in “kill” during a trade session, causing your bot to log you out of MTGO. Combined with the “pass” command, this could be used to steal your password, log you out, and let the bot author log in.
- One account, “Galaphile”, gets autotransfer rights if you don’t specify an autotransfer account.
- One account, “WalkerBoh_”, gets autotransfer rights no matter what you do.
- I think a few accounts get insane levels of credits when they open a trade (no matter what credits.txt says), which makes them just as dangerous as the autotransfer accounts.
Quick word of warning I hadn’t thought of when first posting this – there’s a very real possibility that CBS Bot has more backdoors, not just the direct HTTP connection. If the author built in a command to do something like give him free credits, I honestly don’t know any way one could detect it with a tool as simple as Wireshark.
And since it’s technically illegal to reverse engineer things thanks to the idiocy that is the DMCA, I can’t make any real recommendations. Just be damn careful if you insist on running a bot you (or a trusted friend) didn’t write.
I’m not a lawyer, but I think this clearly falls under the exceptions for Security Testing in Section (j)(3)(a) of the DMCA, assuming you have legally obtained rights (you paid for the software) to use a copy the copyrighted work in question.
UPDATE
Good news – the latest version, 1.32, no longer sends your mtgo password at the start of the app. It instead sends a dummy string, “erijcnfd!uaQncdDeceiJZnce”.
I don’t know that I’d consider the bot safe at this point (in fact I can guarantee it isn’t, but I can’t offer solid proof), but it’s better than it was before.
I’d be very concerned about a so-called ‘dummy string’ like erijcnfd!uaQncdDeceiJZnce .
Sounds exactly like an encrypted version of your password to me – a version of the password you won’t recognise, but that is your pass none the less.
I don’t think that is a dummy string. I believe it’s the same information encrypted.
Andrew, rasguy, I actually considered that at first, but after some investigating, that string is exactly the same no matter what user or password you type into the bot. I can’t figure out why the author did that, other than perhaps to claim that it’s always been like that or something. Or maybe to confuse me into trying to decrypt it.
As I posted over on the Magic forums, this is both terrifying and awesome. I haven’t been so interested in a scandal like this since Limbo of the Lost. You’re a genius for figuring this out, well done.
what’s a safe bot to use?
No idea…. I’ve found one that actually looks like the ripped-off version of CBS the author was talking about. So if anybody finds a legit bot out there, I’d LOVE to hear about it!
Hi, After the problems posted on the gleemax forum about this bot i went looking into Reverse Engineering the bot cause i want to know what the maker was able to see (paypal pass maybe?!?!). But since i’m not exactly a computer genius it didnt work out for me although i found a program that should give you the opportunity to take a look into the code (coded with autoIt3 i believe). On this forum: http://defcon5.biz/phpBB3/viewtopic.php?f=5&t=234&st=0&sk=t&sd=a&start=50 you can read about how to get the code.. It doesnt seem to work for me atm, but ill try to contact the programmer of myAut2Exe if he could help me out here..
Ill keep you posted…
Yeah, I had some other tips, but it appears the latest obfuscator is just insane, so none of my contacts has had much luck really checking out the latest bot.
I continue to be botless, but better that than having my computer compromised, I suppose.
Hi, wow i started playing today since mtgo v2 and i see this whole mess with cbs. I remember the good old yatbot that used to be good. I was gonna use cbs but i think i wont know. Im gonna start developing a yatbot like bot that trades cards for cards and cards for tix ive done bots for mmorpgs and for mtgo v2 so im expecting a beta version 2 months from now well xmas is near so maybe earlier lets see if i can get most of the job done during these vacations. I warn you guys its gonna be a basic bot, dont expect anything better than trading cards for cards or tix untill 2-4months after the realease of the basic bot. Only issue is you might need a dual-core quad-core to run more than one bot.
Ok im not an expert in any field of some sorts, but i was reading this and it got me thinking isnt it possible to run a program that blocks ALL internett connections except from the required to wizards, i bet they have spesific adresses like login.mtgo.wizards1.com for example and such? and just block everything apart from the ones your really need?
I’m betting somebody could do this pretty easily with a small amount of research.
However, that will no longer allow one to run the bot – it now stores all data remotely, so if you don’t allow it to contact the CBS site, you effectively have no bot. I keep meaning to write a “mock” site so that a little hackery (/etc/hosts kind of thing, but for windows) could allow me to run a “safe” bot, but the work involved just isn’t worth it….
And that’s not even the full problem – it could be that the software still has password-stealing mechanisms where the author types in a special command and your bot spits out the password in a trade window. I don’t know if this is the case, but it’s not something I can rule out easily these days.